Is it safe to open securedoc.html (Cisco Registered Envelope)?
I last got one of these in 2010 and assumed it must have died by now, but no, otherwise sensible organisations are still training their customers to fall victim to phishing attacks by asking them to open dodgy email attachments.
The product in question is Cisco Registered Envelope and it deals with the lack of security in email by sending you an encrypted HTML file. Opening this file sends you off to register on some website and then runs a Java app to decrypt the message. This is insane. The HTML attachment in insane and the Java applet is insane.
The latest email I got in this format was an appointment reminder from UCSF. I'm sure there is some HIPPA requirement that they can't just send medical information in a plain text email. But they could send an email that lets you know you should login to your account to see the appointment. It's not like the securedoc.html method is magic, you still have to create an account on a website to use it so it buys you literally nothing.
UCSF, shame on you. Look after your patients digital health as well as their physical health. Out of self interest if nothing else, nobody can pay you if their bank accounts have been emptied after falling victim to a real phishing attack.
Cisco, shame on you. This product is so wrong headed it's impossible to believe that you're doing anything right.
(previously)
Related Posts
You Might Also Like
- Timelapse of three Starlink Trains
- Snowy Egrets at Marshall's Beach
- Merging Resource Dictionaries for fun and profit
(Published to the Fediverse as: Is it safe to open securedoc.html (Cisco Registered Envelope)? #etc #securedoc #cisco #phishing #ucsf #hippa Securedoc.html looks like a phishing/malware attack but isn't. Here's why it's dangerous anyway. )
Overvalidation
Overvalidation is unhelpful error checking, usually caused by an over-zealous engineer with insufficient domain knowledge. My blood pressure has suffered from two cases of overvalidation this week.
I bought a new NAS — the Linksys NAS200 to set up RAID 1 with a couple of 1TB drives.
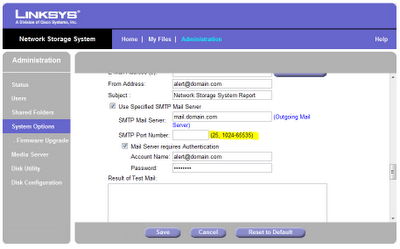
I was delighted to discover that the NAS could send email when it detects a problem or starts running out of disk space. Except it couldn't because someone decided that an email server could live at port 25, or at port 1024 or higher.
My ISP blocks port 25 - maybe to cut back on bot spam, maybe because their support staff are bored and lonely. This is far from unique and it's common for email providers to offer an alternative port. Which is almost always port 587. I tried to put a bug report into Linksys but their support pages effectively said "dude, you paid $89 for this box, go talk to other losers on some forum".
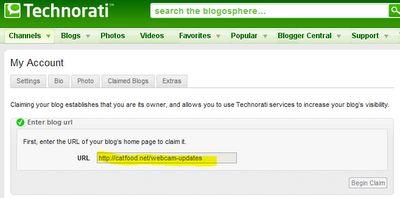
The NAS problem can be solved by redirecting a port on my router. I haven't figured out how to deal with Technorati yet. After spending seemingly months moving their datacenter they've evidently done some work on their blog claim process. I created a new blog yesterday (Webcam Updates, to remove some clutter from the main Catfood Blog) and went over to Technorati to claim it.
When you enter a URL like "http://www.site.com/blog" it's automatically changed to "http://site.com/blog". Which is a different URL. I 301 redirect any "catfood.net" url to "www.catfood.net" to prevent getting dinged by Google for duplicate content. Technorati's claim process fails if there's a 301 redirect.
I guess I could remove the redirect, complete the claim and then hope that I can put the redirect back without breaking Technorati. Possibly when my blood pressure is back to normal.
Please, by all means do some validation – "giraffe" is most certainly not a valid TCP/IP port – but don't overvalidate, and don't assume that your mail server port or preferred URL convention is some kind of universal constant.
Related Posts
- Securing the Internet of Things
- Air Gap
- How to get technical support without spending hours on the phone
You Might Also Like
(Published to the Fediverse as: Overvalidation #etc #cisco Overvalidation: when an engineer doesn't know what they don't know. )